Table of Contents
Introduction:
It refers to information technology (IT) systems and solutions used within an organization without explicit approval or oversight from the IT department. This can include software, applications, or services that employees adopt independently to meet their needs, often bypassing official channels. While it may provide quick solutions, shadow IT can pose security risks and create challenges for IT management and governance.
Thank you for reading this post, don't forget to subscribe!
Image credit: Google search.
It is not limited to tech companies but Deployment and operating shadow IT can lead to serious negative outcomes for businesses in almost all spaces. As per research by Kaspersky, in India, 89% of companies suffered cyber incidents in the last two years, and 20% of these were caused by the use of shadow IT. The IT industry had been the hardest hit, suffering 16% of cyber incidents due to the unauthorized use of shadow IT in 2022 and 2023. It was followed by infrastructure, and transport & logistics organizations, which saw 13% of cyber incidents due to unauthorised use of shadow IT.
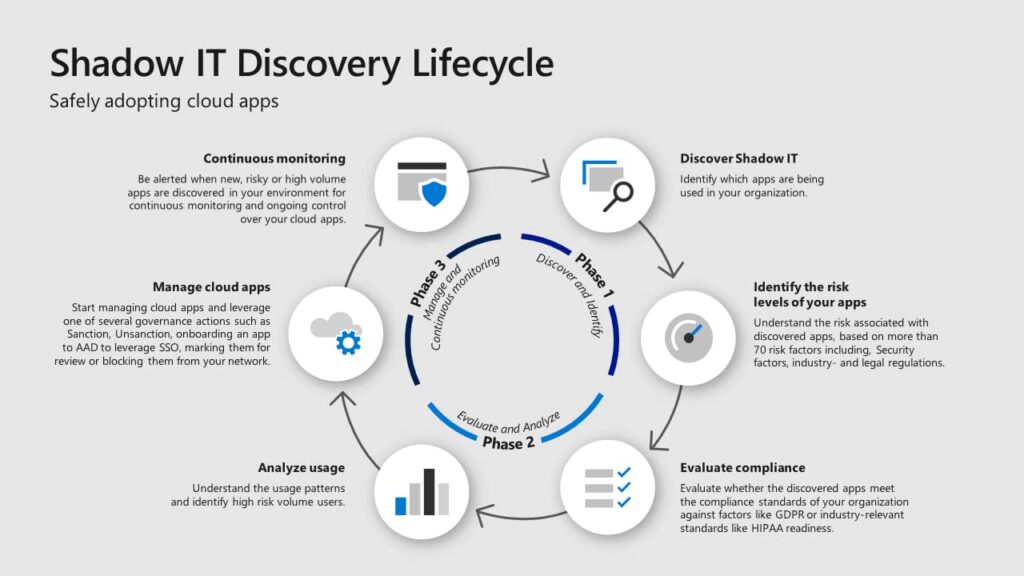
Image credit: Google search.
Meanwhile, 11% of companies worldwide have suffered cyber incidents due to the use of this by employees in the last two years.
Examples:
An example of this could be an employee using a cloud-based collaboration tool or file-sharing service without obtaining approval from the IT department. Instead of using the company-approved collaboration platform, the employee may opt for a convenient tool to share documents or communicate with colleagues. This can lead to potential security vulnerabilities and difficulties in managing and securing sensitive company data.
How to safeguard against Shadow IT-led hacking-
The best way to plug Shadow IT-led hacking is to only use apps installed on employee devices and refrain from using unsolicited flash drives, mobile phones, and laptops. Abandoned hardware left over after the modernization or reorganization of the IT infrastructure can also be used ‘in the shadows’ by other employees, potentially exposing the company to hackers.

Image credit: Google search.
A regular check on the inventory of IT assets like abandoned devices and hardware can also help in eliminating the risks of hacking. Furthermore, making users aware of ways that pose cyber risks can also help in plugging loopholes.
Source Credit: Time Of India.
- FASTag KYC update: Updation of KYC for FASTag before 31st January; Step-by-step Process:
- Tejas vs. Thunder: China’s “Wrestles,” JF-17 With a fighter deal with Nigeria, India’s LCA Tejas is fully engaged in backchannel diplomacy.
- Real Madrid Victory: At Las Palmas, Aurelian Tchouameni gives Real Madrid a late victory.
- Bharat Ratna: Must-know Facts and Important FAQs on the Bharat Ratna Award
- Klopp is leaving Liverpool at the end of the season
